IP 131.137.250.51 – Department of National Defence
Reverse-Attribution Technical Report: IP 131.137.250.51 forces.gc.ca Subdomains
Executive Summary
Forward DNS resolution of IP 131.137.250.51 under the control of the Department of National Defence (DND) reveals underlying dependencies on several forces.gc.ca subdomains. Although external access is denied, the naming conventions and observed error states provide sufficient metadata to attribute the systems to specific DND/CAF functions. These findings highlight that DND-controlled infrastructure remains exposed at the DNS level, offering insight into allied coordination, UAV operations, RCAF applications, and core personnel management.
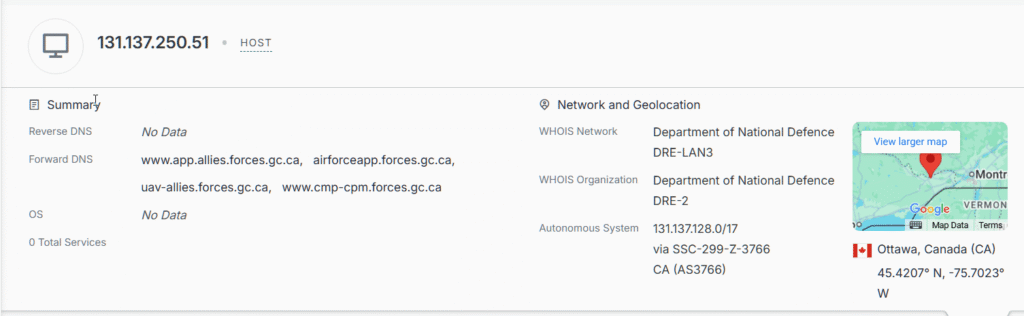
Findings
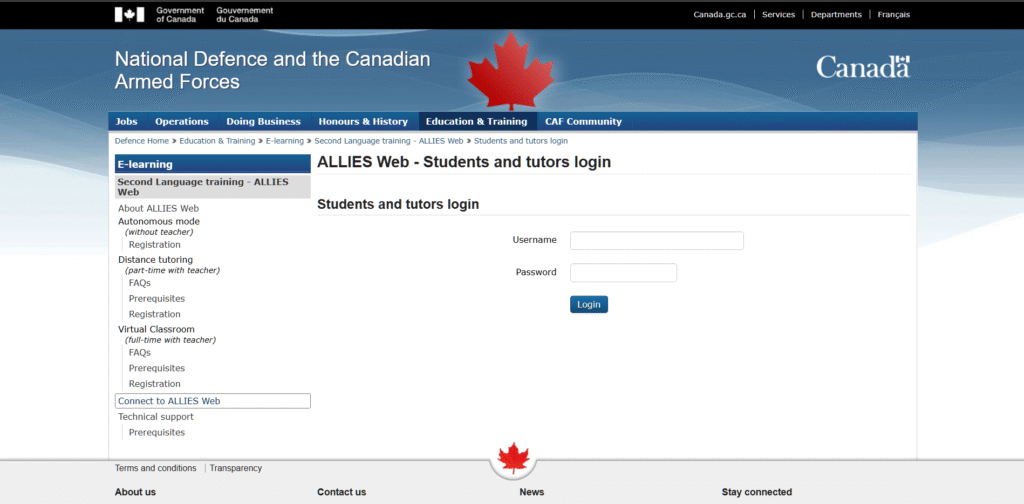
1. www.app.allies.forces.gc.ca
- Observed Response: 403 Forbidden – You do not have permission to view this directory or page.
- Publicly Documented Function: The “ALLIES Web” platform (Autonomous Language Learning in Interaction with Elements in Synergy) is the Canadian Armed Forces’ official online system for second-language training (English/French). CAF members and DND employees use it to practice reading, writing, listening, and speaking, track progress, and prepare for Second Language Evaluations. It supports self-directed study, distance tutoring, and virtual classrooms.
- Assessment: This is a personnel training application operated by DND for internal language maintenance. The restricted access behaviour aligns with its intended design — login-gated for CAF/DND members only. It is possible that it is also being used to train foreign language allies, for example Ukrainians, although this is speculative.
- Confidence: Very High – a login page for the “Allies Web platform” was publicly accessible on September 20, 2025: Additionally, full PDF documentation of the “ALLIES Web” platform training plan for the website, originally published on “Canada Buys,” is available here:
2. airforceapp.forces.gc.ca
- Observed Response: 403 Forbidden – Access denied.
- Interpretation: Tied directly to the Royal Canadian Air Force (RCAF). The “app” suffix suggests a functional, user-facing application rather than a static site.
- Assessment: Likely supports RCAF operational or administrative functions, such as flight planning, weather services, or internal dashboards. Potentially related to applications to the Air Force. ATIA pending.
3. uav-allies.forces.gc.ca
- Observed Response: 403 Forbidden – Access denied.
- Interpretation: Explicitly labelled “UAV” with “allies,” indicating a coalition UAV coordination or intelligence-sharing portal or association with the general language learning program administered by the Canadian Armed Forces
- Assessment: Suggests an established capability for joint UAV operations or information-sharing or a language school, even if currently legacy or test infrastructure.
4. www.cmp-cpm.forces.gc.ca
- Observed Response: Certificate mismatch error (TLS subject does not match hostname).
- Interpretation: CMP = Chief of Military Personnel (CAF directorate responsible for HR, recruiting, training, and administration).
- Assessment: Almost certainly an internal personnel system (HR/pay/records portal). Certificate misconfiguration indicates either legacy hosting or insufficiently updated infrastructure.
Attribution
- Domain:
forces.gc.ca→ reserved exclusively for Department of National Defence (DND) / Canadian Armed Forces (CAF). - Control: Infrastructure is DND-controlled, though network administration may fall under Shared Services Canada (SSC).
- Organizational Links:
- Allied portals: coalition coordination (potential NATO/Five Eyes usage).
- Branch-specific apps: RCAF.
- Personnel systems: Chief of Military Personnel (CMP).
OSINT / Security Implications
- Metadata Exposure
Even without content access, subdomain labels leak organizational functions (allies, UAV, CMP). - Perimeter Posture
Access is blocked (403 responses), demonstrating effective external restriction. - Certificate Mismanagement
Mismatched TLS certificates on CMP portal indicate potential legacy or vulnerable infrastructure. - Reverse-Attribution Value
Confirms direct DND/CAF control, providing clear ownership attribution for investigative, legal, or academic purposes.
Conclusion
The discovery of these subdomains demonstrates how DNS and error-state analysis alone can attribute infrastructure to specific Canadian military functions. While the hosts remain restricted from public access, their naming conventions provide visibility into sensitive operational domains — allied collaboration, UAV operations, RCAF applications, and personnel management.
These findings reinforce the value of reverse-attribution as an OSINT technique, exposing organizational structure even where direct access is denied.
Reverse-Attribution OSINT Report:
No Findings
Additional Details
IP Address: 199.212.150.6
Department/Agency: Department of National Defence
Reverse DNS: No Data
Forward DNS: www.app.allies.forces.gc.ca; airforceapp.forces.gc.ca; uav-allies.forces.gc.ca; www.cmp-cpm.forces.gc.ca
Confidence Level: Very High
Surveillance Level: Undetermined
Automation: no
Notes: Formerly used for hosting Publications of the Canadian Military History Commission (in French: Publications de la Commission d’histoire militaire canadienne).
Sources: Censys, WHOIs

It’s interesting to see a reverse-attribution report focused on a specific IP in the Department of National Defence, which reminds me of some related cybersecurity discussions I found referenced on other great sites.
Interesting report on this IP address and its connection to the Department of National Defence.