The Shared Surveillance Canada Methodology
The Shared Surveillance Canada project, a joint initiative by Prime Rogue Inc, the Federation for Accountability, Freedom and Oversight (FAFO) Labs and Maple Leaks, is an ambitious project to reverse-attribute and investigate the entire IP range of Shared Services Canada, the IT backbone of the Canadian federal government, and other Canadian Departments and Agencies with separate IP ranges. The Shared Surveillance Canada Project is in no way affiliated with Shared Services Canada or the Government of Canada. It is an independent public interest project. The methodology for this project is based on a long-term orientation that is pragmatic, methodical and oriented towards combining structured analytical techniques, defensive cybersecurity measures, and OSINT analysis for the purposes of identifying which governmental department or agency controls a given Shared Services Canada IP.
This project exists because of a changing digital privacy landscape in which it has become apparent that, whether they are fulfilling Privacy Act requests while unlawfully looking up the social media of a requester or unlawfully investigating the social media activities of an indigenous activist, Canadian federal governmental institutions regularly engage in overreach relative to their mandates, and illegally collect information about ordinary Canadians in violation of the Privacy Act and various Charter protections. It is important to note that there are many valid reasons why governmental departments and employees visit public websites. While Shared Surveillance Canada documents these in order to be thorough, these are not the principal focus of our investigations. Rather, our principal goals are to fully reverse-attribute Shared Services Canada infrastructure, and identify those IPs engaged in extra-judicial content intake.
Because of the immense number of IPs under the control of the Government of Canada, and the fact that some of these do not explicitly fall under the IP range publicly attributed to Shared Services Canada, the scope of this project will evolve over time. As noted in the Shared Surveillance Canada Project Overview, the goal of this project is to foster governmental transparency in relation to the digital activities of the Canadian federal government. Some IPs, labelled with the special categories below, feature far more data pertaining to governmental employee use of governmental infrastructure for non-work purposes that is documented for the public interest.
Phase #1: Prioritization
Given that Shared Services Canada administers over 135,000 discrete IP addresses, Shared Surveillance Canada is a multi-year project that proceeds on the basis of efforts by volunteer contributors. The prioritization of IP reverse-attribution proceeds on the basis of the following priority order:
- IPs referred by contributors or members of the public: IPs discovered to be engaged in surveillance or IPs submitted by users on this basis are analyzed first as active use for surveillance purposes is the most important basis for actionability.
- IPs that have been erroneously attributed or which have undergone a change or rotation in allocation: As discussed in relation to confidence levels, attributions can be wrong pending ATIA-based confirmation. Corrections thus occur, and no IP is reverse-attributed in a “final” manner until confirmed via ATIA. IPs can also be rotated or assigned to a new department or agency and any indicative of this leads to a new reverse-attribution.
- IPs associated with a known forward or reverse DNS: IPs attributed with forward or reverse DNS records are prioritized next because Shared Services Canada, with notable exceptions, tends to cluster departmental IP allocations. This thus means that, with notably exceptions, Shared Services Canada IPs hosting websites or pingable servers will be adjacent to other IP spaces under the control of a given department.
- IPs adjacent to known forward or reverse DNS IDs: These are prioritized based on the clustering logic discussed above.
- Other IPs: Shared Surveillance Canada contributors will often select a range of IP addresses to either examine a whole sub-allocation or a random sample to contribute to the project’s prioritization through inductive discovery. Additionally, sponsors and donors may request that we proceed with the reverse-attribution of a given block.
Phase #2: Reverse-Attribution
The second phase in the Shared Surveillance Canada methodology is reverse-attribution of the IP itself. In reverse-attributing Shared Services Canada IP addresses, Shared Surveillance Canada has three main goals:
- Determining the Department/Agency that is in control of the IP assigned by Shared Services Canada.
- Determining the purpose for which the Department/Agency which is in control of the IP makes use of it for.
- Determining whether the Shared Services IP Address in question has been associated with automated surveillance or the mass ingestion of content.
Cases vary significantly in their difficulty. For mainline and simple cases, the Shared Surveillance Canada project makes use of the following tools:
- WHOIS query: A WHOIS query is a basic reverse attribution taking place in the Linux shell which simply queries ownership of a domain. In most cases, as per the image below, a WHOIS query of a Shared Services Canada domain will simply yield the conclusion that it is administered by Shared Services Canada. In other cases, it may yield a server hosted on the IP.
- Censys/Third Party Queries: Censys and other third party queries are used to perform deeper analyses of IPs than those possible with WHOIS alone. With proprietary tools developed by Prime Rogue Inc and other tools allowing for more detailed network analysis, these can supplement WHOIS alone in terms of facilitating reverse-attribution. Over time, third party queries will be shifted to the new version of the Prime Rogue Inc Recon OSINT Suite as it provides for the integration of all the core functions of third party tools.
- OSINT Analysis: In cases where neither a WHOIS query or a Censys/Third Party query yields a clear reverse-attribution, Shared Surveillance Canada personnel or volunteers will proceed to engage in an OSINT analysis of public trace records associated with the IP address. Typically, this involves a combination of traditional search engine techniques, Google Dorking and other analytical strategies. Thankfully, for the purposes of Shared Surveillance Canada, many employees of the federal Government of Canada employee very sloppy operational security practices. From editing Wikipedia entries and signing with their IP to signing trades in fantasy hockey leagues, we are often able to use open-source methods to trace an IP to an individual Government of Canada employee, and then determine if we can prove with a high degree of certainty that this employee worked for a given Agency/Department at the time when the logged event took place. It is important to note that, absent matters of clear public concern or scandsal, Shared Surveillance Canada will publish the methodology used to reverse-attribute based on OSINT info but will not publish the name of the individual themselves unless it is directly present on a screenshot of the activity.
- Access to Information Requests: The Access to Information Act allows Shared Surveillance Canada to request information from Shared Services Canada regarding which government department controls a given IP address. In fact, past Access Requests by Prime Rogue Inc and individual contributors have been successful in retrieving workstation and mirror server logs for alleged surveillance incidents, and these are documented with special category tags in the Shared Surveillance Canada database.
- Why not get all of the reverse-attributions by ATIA?: ATIA requests must be reasonable and must not abuse the right of access. It would be facially unreasonable, under the statute, to request that Shared Services Canada document every single IP under its control in one fell swoop. Such a request would likely also take multiple year to complete based on the right to take an extension present in the Stature. As such, it is more expedient and thorough to proceed through this type of analysis.
Phase 3: OSINT Investigation
OSINT investigations in the Shared Surveillance Canada project have two interrelated but iterated functions:
- When it is not possible to reverse-attribute a domain on the basis of technical analysis, OSINT analysis can provide detailed clues facilitating attribution.
- When a domain has been reverse-attributed with high confidence and Shared Surveillance Canada wishes to determine what type of activity it is regularly used for. When a domain has been reverse-attributed with a degree of confidence of higher or better (discussed below), an OSINT investigation then take places. These are fully legal, as they are based only on public domain information,
Phase 4. Confidence Levels
The following confidence levels are used by Shared Surveillance Canada:
- Very Low: A confidence level of 25% or lower. It is used very seldomly, and only when an OSINT investigation yields a circumstantial connection to a given federal department or agency.
- Low: A confidence level of between 25% and 49% when attribution is based solely on speculative or inferential or circumstantial OSINT analysis.
- Medium: The typical confidence level for an OSINT-based attribution where the IP has been linked to a specific employee of the federal government via OSINT analysis, but without technical corroboration, but wherein Shared Surveillance Canada is still awaiting completion of an ATIA request confirming whether or not this department is typically in control of the IP question.
- High: A confidence level of over 75% that is made use of for an IP that has been successfully technically reverse-attributed based on WHOIS or a third party query that shows an affiliation but no linked publicly pingable server. These requests are also then subject to ATIA requests for subsequent confirmation.
- Very High: A confidence level of over 90% that is typically established when reverse or forward DNS records clearly indicate association with servers linked to a given agency or department. These IPs are also then then subject to ATIA requests for official governmental confirmation.
- Confirmed by Government: Only used when an ATIA request or other government source has confirmed the control of an IP block relative to an institution or agency of the government of Canada.
In discussing confidence levels, an attendant degree of complexity is present in the reverse-attribution process undertaken by Shared Surveillance Canada. This is because some records might actually be misleading. For example, Shared Surveillance Canada will typically assign a confidence level of “very high” when either WHOIS or Censys queries demonstrate a reverse or forward DNS indicating that a given IP address is under the control of a specific institution. That being said, and looking at the example below, it is easy to see that the WHOIS query, showing a registration year of 1993 and an update year of 1995, shows that the domain is apparently under the control of the Solicitor General of Canada.
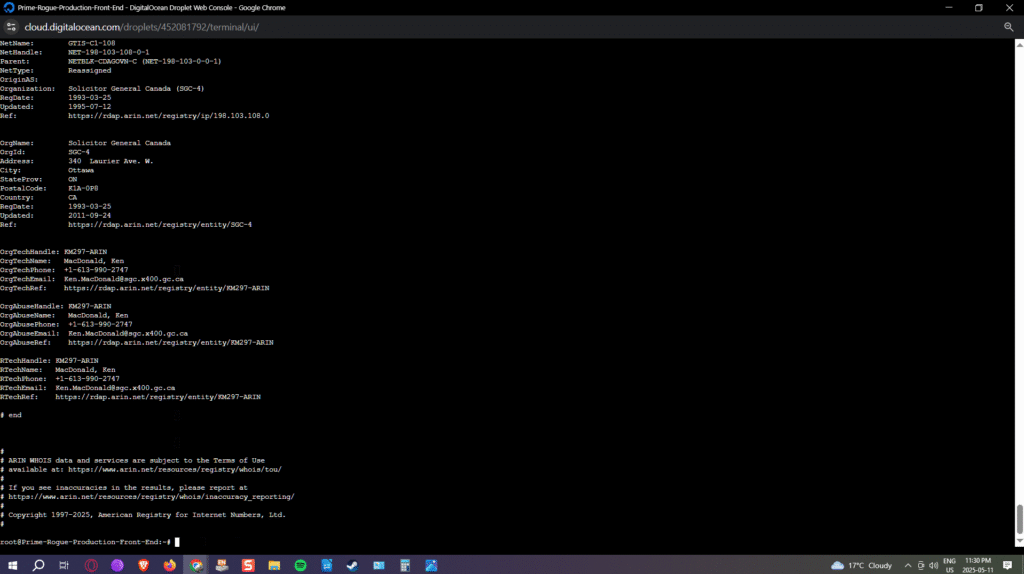
Problematically, the Office of the Solicitor General of Canada was abolished on April 4, 2005, and this led to the creation of the Minister of Public Safety and Emergency Preparedness. It would be highly logical, based on this fact, and the crawling patterns experienced by Prime Rogue Inc, in this particular case, that the address would now be under the control of Public Safety Canada. That said, this is based on inference, and it is an uncertain conclusion. As such, and because the inference is plausible and more than 50% likely to be correct, based on the balance of probabilities test, the confidence level of the attribution drops to Medium. As discussed below, however, cases such as these will receive higher degrees of confidence over time as the Shared Surveillance Canada project submits Access to Information Act requests to Shared Services Canada in order to confirm which agency or department is in control of an IP address.
In contrast to the case of this former Solicitor General of Canada IP, with a medium level of confidence, the screenshot below, from Censys, shows a reverse-attribution that has been given a “Very High” level of confidence for IP 199.212.150.5 being attributed to the Royal Canadian Mounted Police (RCMP). The presence of a named server, in this cased DRAGON, in association with the IP, directly connects it to infrastructure verifiably under the control of RCMP.
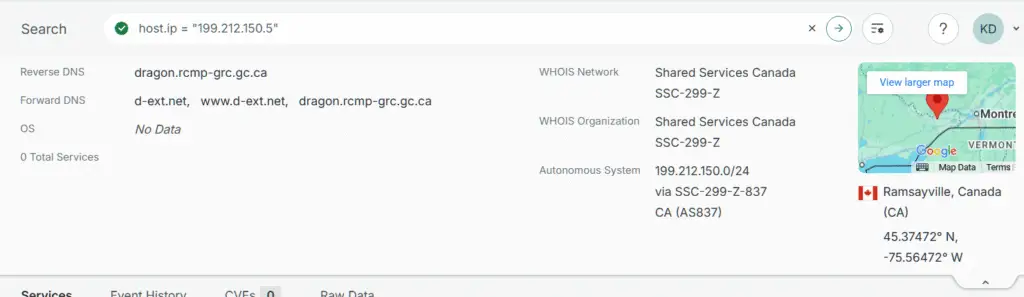
When such a high confidence attribution has taken place, and in a case like 199.212.150.5 where confirmed surveillance has occurred, an ATIA request is sent to the government requesting mirror server logs. Additionally, an OSINT investigation of the domain’s use is then conducted in order to determine what it is typically used for.
Phase 5: Surveillance Level
A surveillance level is only assigned to a government IP block if it has been engaged in the systematic monitoring of the content of a website owned by a contributor to Shared Surveillance Canada or a member of the public who has submitted server logs. Shared Surveillance Canada understands that governmental officials may and can visit public websites in the course of their ordinary duties. It can be very challenging to differentiate between ordinary web visits and systemic government surveillance. As such, Shared Surveillance Canada makes use of the following scale:
- Undetermined: currently the most common surveillance level – used to characterize an IP for which Shared Services Canada has not received any reports of governmental visits.
- Routine: Traffic that appears, based on technical analysis, to be purely routine browsing by a governmental employee.
- Low: Used for cases in which Shared Surveillance Canada has documented one-time governmental visits to a website, based on reverse-attribution, and these appear to be human in nature but not associated with the routine course of the Department’s functions or mandate.
- Medium: Used for cases in which Shared Surveillance Canada detects 3 or less governmental visits to a website, based on reverse-attribution, and no use of automation or obfuscation is evident.
- High: Used for cases in which Shared Surveillance Canada detects any number of governmental visits to a website, based on reverse-attribution, and any form of obfuscation is used.
- Very High: Used for cases in which Shared Surveillance Canada detects any number of governmental visits to a website, based on reverse-attribution, and any form of automation is used.
- Orwellian: Used for cases in which Shared Surveillance Canada detects governmental visits to a website involving automated mass ingestion of content or confirmation, via ATIA or other means, that a governmental institution with no mandate for information collection has been confirmed to be engaged in reputational monitoring or other activities in relation to a website.
Surveillance Automation
If surveillance is detected, Shared Surveillance provides a dichotomous yes/no determination of whether it is believed that this surveillance was automated. This determination is made by a Shared Surveillance Canada contributor with technical expertise, and the methodology for detecting automation is typically premised on a combination of request timing, browser spoofing, content volume, and other variables. Shared Surveillance Canada makes use of the “balance of probabilities” test, and labels the IP as engaged in automated surveillance if it is believed, at a confidence level of more than 50%, that the visit/collection was automated.
Phase 6: Additional Notes
Shared Surveillance Canada makes use of many forms of additional notes for its reverse-attribution efforts, and we regularly add new categories based on the discover of new forms of governmental activity taking place on work computers. These are based on technical and OSINT analysis and include the following:
Confirmed Surveillance
The Confirmed Surveillance category is used when server logs demonstrate government content ingestion that is not legitimately associated with a government function in terms of either substance or volume.
Fantasy Sports Fanatics
The Fantasy Sports Fanatics category is used for an IP reverse-attribution where OSINT investigation reveals that a given governmental IP address was used to participate in fantasy sports activities while at work. Such conduct is documented within the reverse-attribution post body.
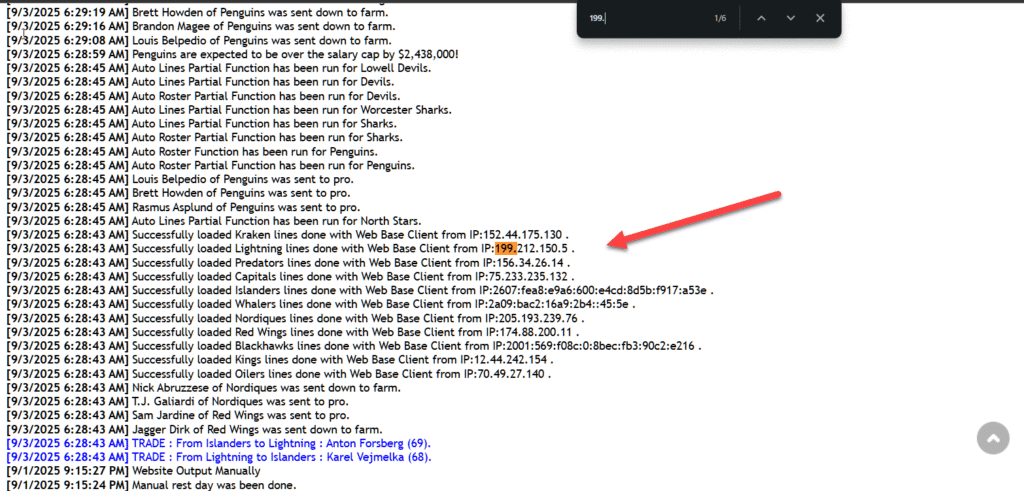
This screenshot from the Dave Charron Hockey League, a bespoke invite-only fantasy hockey league, shows an individual using RCMP infrastructure to sign trades on their fantasy hockey league while controlling the Tampa Bay Lightning. Fantasy hockey is perhaps the most commonly discovered form of personal use of governmental infrastructure and, because trades tend to be signed by IP address, fantasy hockey league usage can highlight significant operational security violations by governmental employees for IP addresses that might not otherwise be successfully reverse-attributed. It also allows for network analysis of connections between departments based on inter-personal relationships.
Forum Fun
The Forum Fun category is used for reverse-attributions where OSINT investigations of an IP address reveal that governmental employees used their work computer to post to a forum unrelated to the Department’s function or activities. Some of the petty squabbles engaged in by governmental employees on these forums are quite humorous, and such conduct is documented within the reverse-attribution post body.
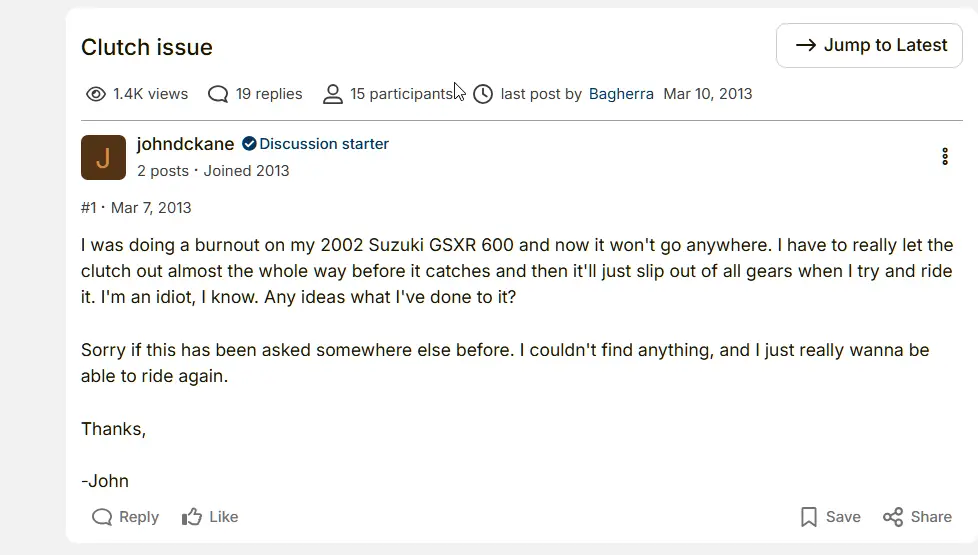
As an example, this post from the Gixxer Forum shows an individual using RCMP infrastructure to post about destroying his Suzuki motorcycle’s clutch while doing “burnouts” on his motorcycle. It is thus categorized by Shared Surveillance Canada as an instance of “Forum Fun.”
Restaurants and Other Reviews
A category that is used for reverse-attribution where OSINT investigations of the IP reveal that governmental employees have used it to review restaurant or other goods and services. Such conduct is documented within the reverse-attribution post body.
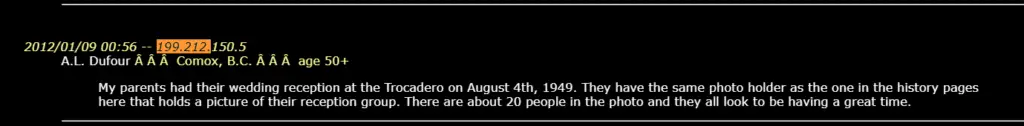
In this example of the “Restaurants and Other Reviews” category, an individual using RCMP infrastructure reviews the “Trocadero” wedding reception venue in Edmonton with what appears to be a name, location, and age. This evidently provides for reverse attribution via OSINT analysis of work affiliations and is in the public interest as it documents how governmental employees use work IP for non-work purposes.
Wikipedia at Work
A category that is used for reverse-attributions where OSINT investigations of the IP reveal that governmental employees have used it to edit Wikipedia entries. Such conduct is documented within the reverse-attribution post body.
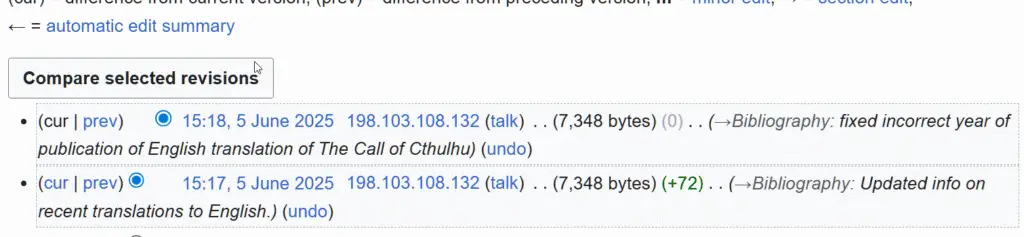
This screenshot shows an employee likely associated with Public Safety Canada editing a manga-related Wikipedia page at work.
Other Categories
Other categories are added as they are documented, and published in the public interest in order to demonstrate personal use of governmental web infrastructure that is publicly available.
Conclusion
The Shared Surveillance Canada methodology is methodical but pragmatic in nature. It makes use of a consistent structure for reverse-attribution and a multi-factorial/vector OSINT strategy for investigation. Its orientation is to help members of the public understand Canadian governmental web activity targeting citizens. Future plans are in place to reverse-attribute provincial IPs and some provincial IPs can be found in the database based on user reports.
If you wish to request a reverse-attribution, please use the form below: